Why Many Studios and Broadcasters are Banning FTP From Their Supply Chain
For decades, FTP (File Transfer Protocol) has been used in the Media & Entertainment (M&E) industry to move files between servers and for distributing them around the world. And for just as long, cybersecurity experts have been warning of its potential threat to network security, intellectual property and privacy. Nevertheless, FTP has persisted.
And it’s no wonder. FTP was designed before the Internet as we know it, before every computer running in a business was connected to a global communication and information exchange network.
Starting as a basic protocol for Internet file transfers when few people had access to the Internet and even fewer had the skills to be dangerous, FTP became entrenched in many company’s technology infrastructures when security threats were mostly theoretical.
Today, it’s hard to imagine a world without the web, but it was only in 1993, when CERN donated its World Wide Web technology to the public domain, that we began this wild era of human hyperconnection. In many ways, it’s been amazing, creating new opportunities for education, business, altruism and social progress. So much has happened in the past 25 years that it’s easy to understand why worrying about a basic Internet protocol hasn’t been top of mind for enterprise leaders.
However, after a few years of regular high-profile hackings that have threatened individual privacy, business intellectual property and more, suddenly, we are all a lot more sober about Internet privacy and security. Perhaps, this industry is now ready to listen to the research and advice of security experts.
Security Reports Continue to Warn About FTP
A 2015 study called FTP: The Forgotten Cloud conducted by the University of Michigan revealed more than 13 million FTP servers in use, with 1 million configured to allow anonymous access, potentially exposing sensitive files and network access. And that number has only grown over the years. A 2019 report by Digital Shadows’ Photon Research Team examined data exposure on the most common file-sharing services across the Internet. They found over 12 petabytes of data exposed through FTP servers, SMB (Server Message Block), rsync, misconfigured websites, Network Attached Storage (NAS drives), and open Amazon S3 (Amazon Simple Storage Service) buckets. (Note that Amazon now sets S3 buckets as private by default). Within the exposed data were more than 1.5 billion exposed files, an increase of more than 50% over the previous year. Older, yet still widely used, technologies — such as FTP (26 percent), rsync (28 percent) and SMB (33 percent) — contributed to the most exposure.
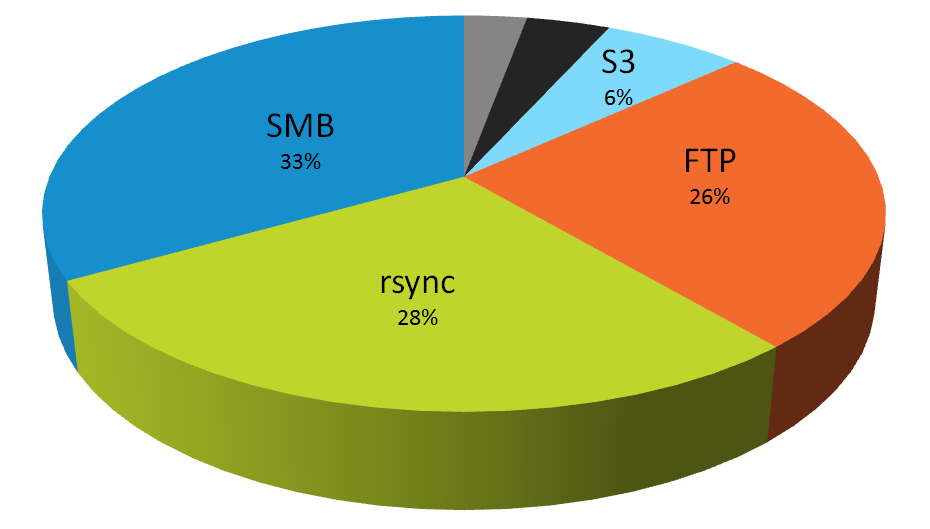
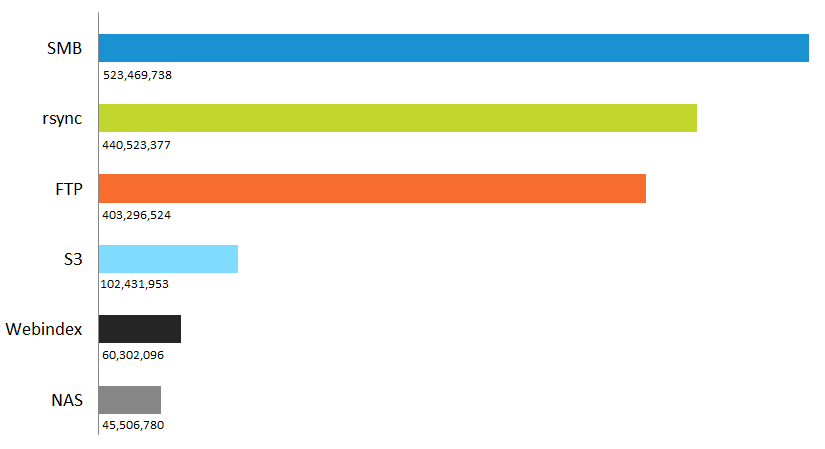
“Our research shows that in a GDPR world, the implications of inadvertently exposed data are even more significant. Countries within the European Union are collectively exposing over one billion files – nearly 50% of the total we looked at globally — some 262 million more than when we looked at last year,” said Harrison Van Riper, a Photon Research analyst.
Considering the proliferation of FTP throughout the M&E industry and how large video files are, loads of that data are probably high-value media assets. We all probably recall the 2017 HBO, Netflix and Disney security breaches. According to Alex Heid, Chief Research Officer at Security Scorecard, those can likely be traced to hackers exploiting FTP used by third-party post-production companies.
“A lot of the time the people doing the editing have access to confidential, highly secure information just so they can access files they need quickly,” said Heid in an interview with Polygon. “The hacker underground has figured out how these transfers are being done and how to get into a company’s main database through that.”
“Using an FTP goes back to the beginning of the internet,” Heid continues. “It’s not a very secure method…There may not be any password in place. But once an attacker has that, they can essentially log in to the entire network.”
It’s important to note that the 12 petabytes of exposed data found by Digital Shadows (26% through FTP) isn’t data that has been accessed by malicious hackers intruding on a network or by phishing campaigns tricking employees or even through corporate espionage. This is data that is unprotected and publicly available to anyone (or any bot) with will to look for it. But there is some good news, maybe.
“The good news is, since most of these protocols pre-date many of today’s security practitioners, there is a wealth of direction on how to mitigate the risks associated with them. Sadly, as the 12 petabytes of exposed sensitive data demonstrates, much of this mitigation advice has fallen upon deaf ears.”
Industry Leaders Push for Higher Security and Performance Standards
In response to all of this, some major media enterprises have completely replaced FTP internally and refuse to work with partners who use it, insisting that all media providers use secure, accelerated transfer solutions. They know that the media industry’s content supply chain is inherently interconnected, and they are not alone in that understanding.
Pushing for higher security and performance standards across the industry in Europe, the Digital Production Partnership (DPP) is one example of an organization that took on the problem. The newly formed Trusted Partner Network (TPN), a joint venture between the Motion Picture Association of America (MPAA) and the Content Delivery & Security Association (CDSA), is another.
In order to stop what Alex Heid called an ongoing series of “repeatable attack scenarios,” security needs to be everyone’s concern and that very well may hinge on a secure FTP replacement.
If you’re looking for an FTP alternative, you’re not alone or at least you shouldn’t be. Major browsers, including Chrome, Safari, and (just recently) Firefox, have blocked FTP subresources from loading inside HTTP and HTTPS pages or labeling FTP sites as insecure.
Yet, even though security experts have long known about FTP’s potential security issues and have been recommending a switch to SFTP (secure file transfer protocol) starting in the late ‘90s, FTP security has only gotten worse. Without support for modern encryption techniques, FTP has become a primary target for malicious hackers and malware distributors.
Security is a New Driver to Find FTP Alternatives
Historically, FTP alternatives were primarily sought out because file sizes had exceeded what FTP could handle. Anything above a few gigabytes becomes difficult to move with FTP, especially over distance. Accelerated file transfer software, such as developed by Signiant, is certainly needed to move large files faster, particularly for companies that have globally distributed teams and tight deadlines like in media production.
However, Signiant has seen a shift in concern. Clients still look to Signiant accelerated file transfer solutions primarily to solve challenges with moving large files quickly, but they are asking a lot more questions about security as well — which Signiant is prepared to handle. As a trusted leader in the Media & Entertainment industry and beyond, Signiant successfully completed the Trusted Partner Network’s (TPN) App and Cloud Gold Shield Assessments for its SaaS products. This rigorous evaluation was conducted by Independent Security Evaluators (ISE), a TPN-accredited assessor with a longstanding reputation as a respected independent technology evaluator in the media industry. Additionally, Signiant’s products are SOC 2 Type 2 compliant, further demonstrating their commitment to security and reliability.
If you are looking for an FTP alternative, particularly for secure, fast and reliable large file transfers between people, systems or to and from the cloud, take a look at Signiant’s product suite. Signiant solutions can either work as an FTP replacement or alongside current FTP systems, taking away the pain of ripping out FTP, while preserving file structures and providing an FTP alternative that is fast, secure and light years beyond in user experience design.


